Unlock IoT Remote Access: SSH On AWS Made Easy!
Ever found yourself locked out, staring at a firewall that guards your IoT devices like a medieval castle? The ability to remotely access and manage these devices, especially those tucked away behind restrictive networks, is no longer a luxuryit's an absolute necessity.
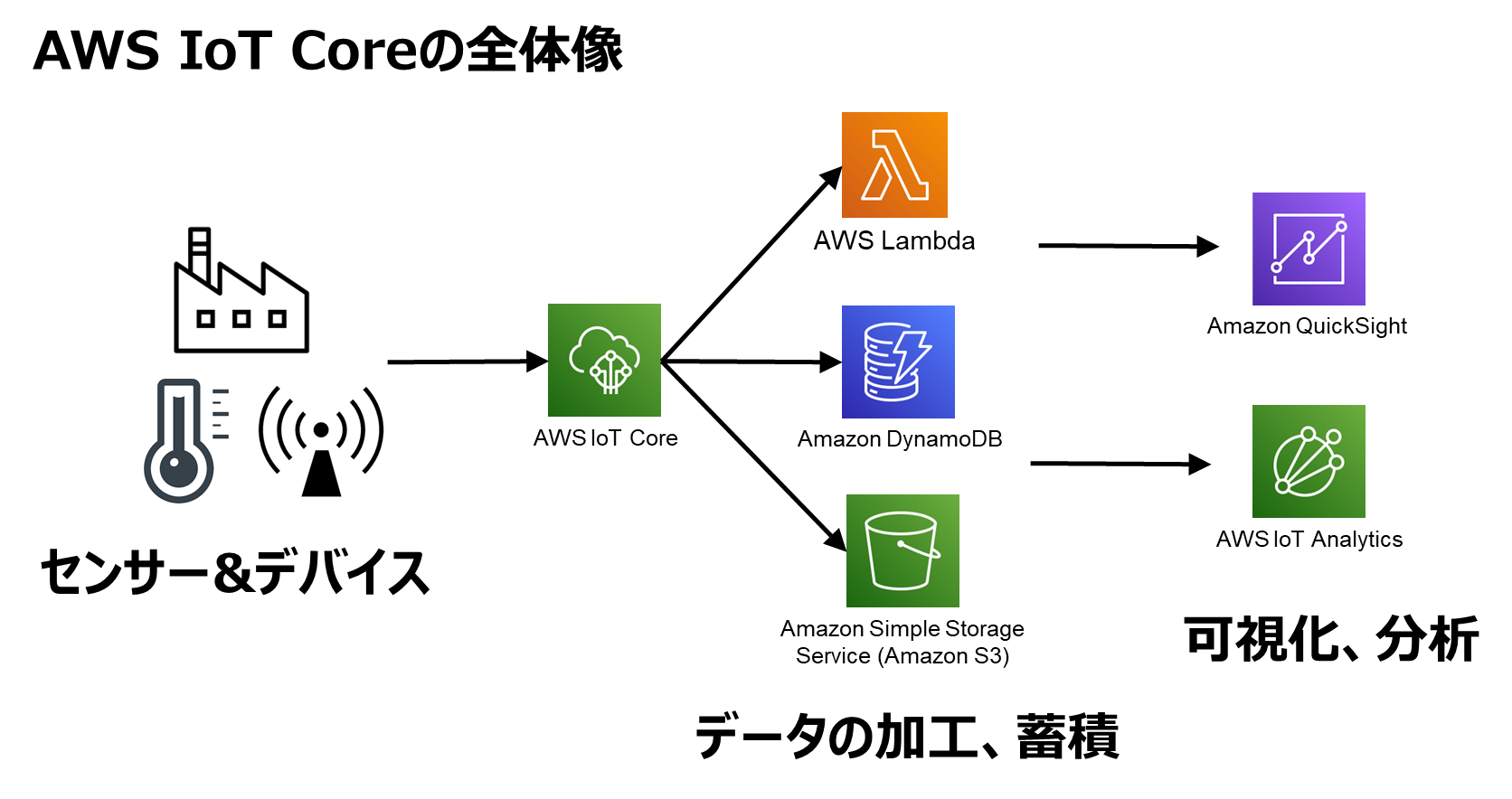
That's where secure tunneling, a powerful feature within AWS IoT Device Management, steps in as a game-changer. It empowers users to perform remote tasks like troubleshooting, configuration updates, and other critical operational duties, without the need to physically be on-site. AWS continuously enhances its offerings to provide customers with even greater capabilities in this space, and this is particularly crucial when IoT devices are deployed in remote locations where physical access is limited or costly. This enables administrators to swiftly address unauthorized activities, preventing potential damage before it occurs.
| Category | Details |
|---|---|
| Concept | IoT Remote Access using SSH on AWS |
| Key Components | AWS IoT Core, Secure Tunneling, SSH, EC2 Instance (optional), IoT Device Agent |
| Benefits | Remote troubleshooting, configuration updates, reduced on-site visits, enhanced security, prevention of breaches, seamless wireless interconnectivity, simplified setup |
| Setup Methods | Quick setup (default configurations), Manual setup (editable configurations) |
| Authentication | Cryptographic keys (username/password or private key the latter may require specific configuration) |
| Use Case Example | Smart Home system with thermostats and security cameras managed remotely through an EC2 instance. |
| AWS Services | AWS IoT Core, AWS IoT Device Management, EC2 (optional), IAM |
| Alternative Approach | Traditional SSH with VPN or proxy connection (for non-AWS users) |
| Further Information | AWS IoT Device Management Official Page |
The advantages of IoT remote access are numerous. Beyond preempting and resolving breaches, it leverages the power of wireless interconnectivity. In 2023, a multitude of tools exist to streamline the setup, configuration, and access of IoT devices. While AWS provides a comprehensive suite of IoT services, those not using AWS can still employ traditional methods such as SSH with VPN or proxy connections. Accessing IoT devices through a virtual private network (VPN) involves configuring the VPN, resolving any connectivity issues, and then utilizing SSH as if on the local network.
- Subhashree Sahu Mms Scandal Unveiling The Controversy 2024 Update
- Sadie Mckenna Nude Leak The Privacy Scandal Explained
The tutorials provided by AWS often focus on creating tunnels using the AWS Management Console and the AWS IoT API Reference. Within the AWS IoT Console, tunnels can be created either from the Tunnels Hub page or directly from the details page of a created "thing." These services, in tandem with SSH, establish a robust ecosystem for secure IoT remote access.
Implementing IoT remote access with SSH on AWS involves a series of well-defined steps. This article serves as a comprehensive guide to help you set up the system efficiently and securely. Secure tunneling provides a remote access solution seamlessly integrated with AWS IoT, allowing you to access your IoT devices from virtually anywhere.
This functionality simplifies the configuration process, thereby reducing the need for physical intervention. Consider the cost savings associated with fewer on-site visits, especially when systems malfunction. Providing remote access capabilities on devices deployed in the field is highly recommended. It enables troubleshooting, configuration changes, access to log files, and other operational tasks to be performed remotely, regardless of the device's location.
- Jimmy Kimmels Huge Pay Salary Net Worth More
- Bollyflix Your Guide To Bollywood Movies Dubbed Series Watch Now
The process typically involves an IoT device agent running on the remote device, which connects to the AWS IoT Device Gateway and is configured with an MQTT topic subscription. For detailed instructions on connecting a device to the AWS IoT Device Gateway, refer to the AWS documentation. This guide aims to provide you with all the necessary information to set up and manage IoT SSH tunnels on AWS, ensuring both security and accessibility of your devices.
In today's interconnected world, the importance of securing remote access to IoT devices cannot be overstated. Secure Shell (SSH) stands as a bedrock protocol for establishing secure, encrypted connections between devices. Let's dive into the world of IoT remote access via SSH on AWS. As the Internet of Things continues its exponential growth, efficient and secure device management has become increasingly critical.
This guide will provide you with the knowledge necessary to set up and manage your IoT ecosystem with expert-level proficiency. Imagine the power of being able to access and control your devices from any location, at any time. Whether you're a developer, an IT professional, or a business owner, mastering remote IoT SSH on AWS is essential for staying competitive in today's fast-paced landscape.
AWS offers a wide array of IoT offerings, facilitating seamless device connectivity and data processing through services like AWS IoT Core. Integrating SSH into this framework empowers users to remotely manage devices, troubleshoot issues, and execute secure updates with confidence.
One of the fundamental challenges in IoT deployments is gaining access to devices residing behind restrictive firewalls at remote sites. Secure tunneling addresses this challenge directly. Secure tunneling is a feature of AWS IoT Device Management which helps customers to perform remote tasks. Quick and manual setup methods are available. You can create a new tunnel with default, editable configurations. To access your remote device, you can only use ssh as the destination service. You need the web interface for managing your aws resources, a tool for connecting to your ec2 instance and iot devices (e.g., putty, openssh), and a set of cryptographic keys used for authentication. An example implementation of IoT SSH on AWS can involve setting up a smart home system where multiple IoT devices, such as smart thermostats and security cameras, are connected to an EC2 instance via SSH. The EC2 instance acts as a central hub for managing and monitoring the devices. This scenario illustrates the practicality and efficiency of secure IoT remote access.
Using SSH to access your IoT devices remotely offers numerous advantages. These include enhanced security, as SSH employs strong encryption to protect data transmitted between the client and the server. Remote access eliminates the need for physical access, saving time and travel costs. SSH enables secure file transfers, allowing you to upload or download configuration files, logs, and other important data. It also supports remote command execution, enabling you to manage and configure devices from anywhere in the world.
A practical example of IoT remote access with SSH on AWS involves setting up a smart home system. In this scenario, multiple IoT devices, such as smart thermostats and security cameras, are connected to an EC2 instance via SSH. The EC2 instance acts as a central hub for managing and monitoring the devices. This setup allows homeowners to remotely control their thermostats, view live camera feeds, and manage other smart home devices from anywhere with an internet connection. Secure tunneling provides a secure, remote access solution that directly integrates with AWS IoT to allow you to access your IoT devices remotely from anywhere. This can simplify the configuration, and reduce the amount of work required to manage remote devices.
To successfully set up SSH access for your IoT devices, youll need a few tools: The web interface for managing your AWS resources, a tool for connecting to your EC2 instance and IoT devices (e.g., PuTTY, OpenSSH), and a set of cryptographic keys used for authentication. Whether you're a developer, IT professional, or business owner, mastering remote IoT SSH on AWS is essential for staying ahead in today's competitive landscape. Environment variables are variables maintained by the operating system and used by system commands. They are not saved if you close the SSH session.
For instance, IDT for AWS IoT Greengrass V2 can use the `aws_access_key_id` and `aws_secret_access_key` environment variables to store your AWS credentials. This provides a convenient way to authenticate your devices without hardcoding credentials in your code. In addition to SSH, AWS IoT offers secure tunneling for remote access. AWS IoT Secure Tunnel provides a secure way to access devices behind firewalls without opening inbound ports. With VPN configured and no VPN connection issues present, connect to your network securely and then access your iot device through SSH as if you were on your local network.
So I can successfully create a secure tunnel over MQTT and SSH login via username and password to the device using the AWS IoT console; however, the option to log in via private key does not work, even with my same private key which works logging in over local network (public key is in .ssh/authorized_keys). This can create challenges for automated deployment scenarios. There is also an option to specify a timeout on the credentials. I recommend keeping this low so that if your tokens get leaked somehow, they will naturally expire.
The option to login via private key does not work. Even with my same private key which works logging in over local network (public key is in.ssh\/authorized_keys). Aws iot secure tunnel list services. Aws iot secure tunnel settings. There is also an option to specify a timeout on the credentials. I recommend keeping this low so that if your tokens get leaked somehow, they will naturally expire. Aws iot secure tunnel timeout. Aws iot secure tunnel timeout settings.
Aws provides a robust ecosystem for Iot deployments, offering services like aws iot core, which facilitates device connectivity and data processing. By integrating ssh into this framework, users can remotely manage devices, troubleshoot issues, and perform secure updates. \u6b64\u4e8b\u7269\u5bf9\u5e94\u4e8e\u4e91\u4e2d\u60a8\u7684\u8fdc\u7a0b\u8bbe\u5907\u8868\u793a\u3002\u6709\u5173\u66f4\u591a\u4fe1\u606f\uff0c\u8bf7\u53c2\u9605\u5728 aws iot \u6ce8\u518c\u8868\u4e2d\u6ce8\u518c\u8bbe\u5907\u3002 \u60a8\u6709\u4e00\u4e2a iot \u8bbe\u5907\u4ee3\u7406\uff08\u8bf7\u53c2\u9605 iot \u4ee3\u7406\u4ee3\u7801\u6bb5\uff09\u5728\u8fde\u63a5\u5230 aws iot \u8bbe\u5907\u7f51\u5173\u7684\u8fdc\u7a0b\u8bbe\u5907\u4e0a\u8fd0\u884c\uff0c\u5e76\u914d\u7f6e\u4e86 mqtt \u4e3b\u9898\u8ba2\u9605\u3002\u6709\u5173\u66f4\u591a\u4fe1\u606f\uff0c\u8bf7\u53c2\u9605\u5c06\u8bbe\u5907\u8fde\u63a5\u5230 aws iot \u8bbe\u5907\u7f51\u5173\u3002
\u30bb\u30ad\u30e5\u30a2\u30c8\u30f3\u30cd\u30ea\u30f3\u30b0\u306f\u3001 aws iot device management \u306e\u6a5f\u80fd\u3067 aws iot \u304c\u7ba1\u7406\u3059\u308b\u5b89\u5168\u306a\u63a5\u7d9a\u3092\u4ecb\u3057\u3066\u3001\u304a\u5ba2\u69d8\u304c\u30ea\u30e2\u30fc\u30c8\u30c7\u30d0\u30a4\u30b9\u306b\u30a2\u30af\u30bb\u30b9\u3059\u308b\u4ed5\u7d44\u307f\u3092\u63d0\u4f9b\u3057\u307e\u3059\u3002 secure tunneling \u306f\u3001\u65e2\u5b58\u306e\u30a4\u30f3\u30d0\u30a6\u30f3\u30c9\u30d5\u30a1\u30a4\u30a2\u30a6\u30a9\u30fc\u30eb\u30eb\u30fc\u30eb\u306e\u66f4\u65b0\u3092\u5fc5\u8981\u3068\u3057\u306a\u3044\u305f\u3081
- Filmyfly 2024 South Movies Your Ultimate Blockbuster Guide
- Remembering Toby Keith Life Music And Lasting Legacy
Unlocking The Power Of Remote Access To IoT AWS Your Ultimate Guide

AWS IoT SSH Tunnel The Ultimate Guide To Secure Connections

IoT SSH Access On AWS A Comprehensive Guide For Secure Device Management